
T-110.5140 Network Application Frameworks P (5 cr)
DHT-IPSec
The target of this assignment is to configure two DHT networks, implement a mediator client transfering data between these DHT networks, and two other clients. Each of these two clients will access a separate DHT network. Moreover, you will also familiarize yourself with securing network traffic between the DHT nodes with IPSec. Any programming language can be used to implement the clients. Bamboo provides example clients in Python.
Distributed Hash Tables (DHT) is a distributed system for storing and retrieving values with a given key. DHTs are scalable in that they can include large number of participating nodes with high churn (nodes leaving, joining, or failing).
DHT implementations are available for several languages. In this assignment you will use the Bamboo Distributed Hash Table implemented in Java (look at the /usr/local/src directory on your assignment environment).
IPsec is a security extension for the Internet Protocol (IP) developed by the IPsec working group of the Internet Engineering Task Force. Unlike transport-layer security protocols like TLS, IPsec works in a connectionless manner on the network layer. This means that IPsec can be used to secure any Internet traffic without application support.
IPsec has two security-related headers: Authentication Header (AH) provides authentication services and Encapsulating Security Payload
(ESP) provides various confidentiality and integrity functionalities.
IPsec can be used in two modes: Transport mode provides security between two end nodes and Tunneling mode provides security between gateways.
The IPsec architecture has been designed to be very flexible so that it can be extended with additional algorithms without changes to the protocol itself. Key management is also possible through many schemes, including configuring keys manually.
Requirements
The goals of this assignment are to
- Learn about DHT and IPSec
- Acquire an understanding of configuring, monitoring, and securing a DHT network
- Learn to implement a DHT client
A completed assignment consists of the following parts:
- Configuration files for each DHT node and testing the DHT networks
- Source code of the DHT clients
- Traffic captures from each phase: after starting up the DHT nodes, data initialization, synchronizing data, and securing the traffic between hosts with IPSec (ESP)
- IPSec configuration files and SAD entries (setkey -D)
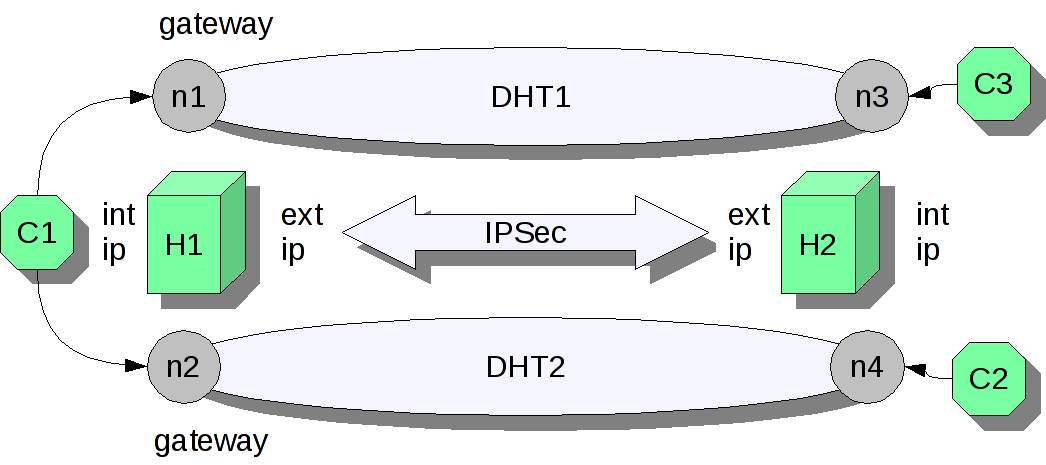
The two DHT networks (DHT1, DHT2) are set up on two hosts. Each host (H1, H2) will run two DHT nodes ((n1, n2), (n3, n4)) belonging to a separate DHT network. Two of the nodes act as gateways.
First, the two DHT clients (C2, C3) initialize data in their dedicated DHT
network with random items (at least 100 items). After this the mediator DHT client (C1) starts transfering data between the two networks aiming to fully synchronize the data in both networks. To accomplish this, the three clients might have a common understanding of the naming of the keys used in the DHT networks. Finally, the DHT network traffic is protected by IPSec. Thus, each of the nodes can see each other in the same virtual network.

